Many companies will have understood the need for a government cyber security standard for their data. We’ve already outlined how the ISO 27001 standard benefits businesses previously. However, military contractors need to conform to a different security standard. The most recent addition to the government cyber security measures comes from the Cybersecurity Maturity Model Certification (CMMC). This certification, as the Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)) informs us, is a unified cyber security protocol that all defense contractors must follow. Because it’s such a novel implementation, many defense contractors aren’t fully aware of what the CMMC entails. In this article, we’ll demystify the CMMC to help contractors understand what’s expected of them.
How Does the CMMC Work?
The CMMC breaks down processes and best-practices in the cybersecurity industry into several domains. The initial draft of the CMMC uses a subdivision of seventeen (17) domains. These are:
- Access Control (AC)
- Asset Management (AM)
- Awareness & Training (AT)
- Audit and Accountability (AU)
- Configuration Management (CM)
- Identification and Authentication (IA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PE)
- Recovery (RE)
- Risk Management (RM)
- Security Assessment (CA)
- Situational Awareness (SA)
- System and Communications Protection (SC)
- System and Information Integrity (SI)
Practices, Capabilities, and Processes for Government Cyber Security
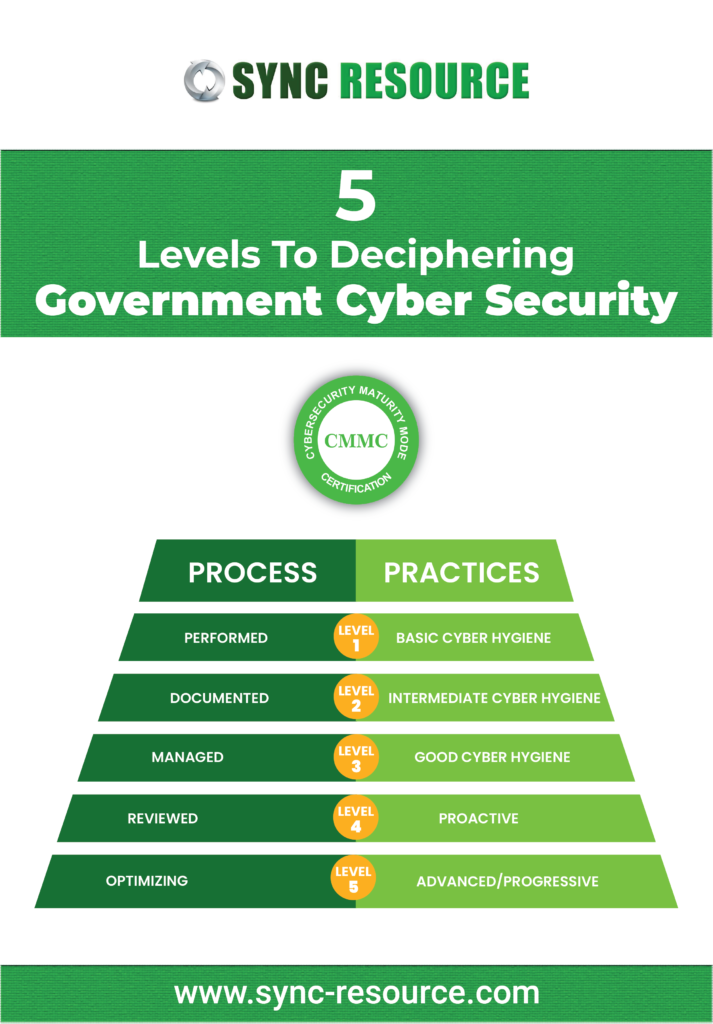
The Government cyber security approach compartmentalizes the qualification and maturity of the abovementioned domains. Each of these domains is split up in processes, capabilities, and practices. Based on the maturity of those practices, processes, and capabilities, the CMMC gives the organization a rating. For each of these delineations, the five levels of maturity differ.
When looking at processes, the five levels of maturity that the CMMC deals with are:
- Performed: the processes were done, and the organization recorded their performance when it was required.
- Documented: The organization reported the process, both when it was needed and when it wasn’t.
- Managed: Documentation conforms to all prior levels, and a plan exists that includes all activities associated with the process.
- Reviewed: The process follows all previous levels and is reviewed for efficiency and effectiveness.
- Optimizing: The process conforms to all lower levels and has a standardized documented approach that all applicable units in the organization rely on.
When it comes to practices, the five levels are slightly different:
- Level 1 Basic Cyber Hygiene:
This level utilizes the Federal Acquisition Regulation (FAR) 48 CFR 52.204-21 as what organizations should already have implemented.
- Level 2 Intermediate Cyber Hygiene:
At this level, organizations conform to level 1 and implement a subset of forty-eight (48) select practices from the NIST SP 800-171 r1. It includes seven (7) new methods to support organizations’ cyber hygiene implementations.
- Level 3 Good Cyber Hygiene:
organizations at this level conform to the previous levels and implement all of the guidelines outlined in NIST SP 800-171 r1. There are an additional twenty (20) practices that aid in cyber hygiene.
- Level 4 Proactive:
This level follows all the previous levels’ guidelines and implements a select subset of eleven (11) practices from Draft NIST SP 800-171B. There are also an additional fifteen (15) practices that allow organizations to demonstrate a proactive cybersecurity program.
- Level 5 Advanced/Progressive:
Organizations that get to this level implement a select subset of four (4) practices from the Draft NIST SP 800-171B. These institutions also demonstrate eleven (11) new techniques showcasing their dedication to an advanced or progressive cybersecurity approach.
What This Means for Government Cyber Security Contractors
Throughout the descriptions of these domains, processes, and practices, it’s easy to see how the CMMC is similar in approach to the ISO standards system. It aims to help contractors establish best-practices that are a habit so that even under pressure, they still follow the appropriate safety measures. Sync Resource has been instrumental in helping out clients achieve CMMC compliance. Let’s advise you on how your company can improve to meet the strict standards set in place by government cyber security initiatives.